In modern application architectures, secure user authentication and authorization are essential. OAuth 2.0 has become the de facto standard for enabling secure delegated access to resources, particularly when working across multiple services and platforms.
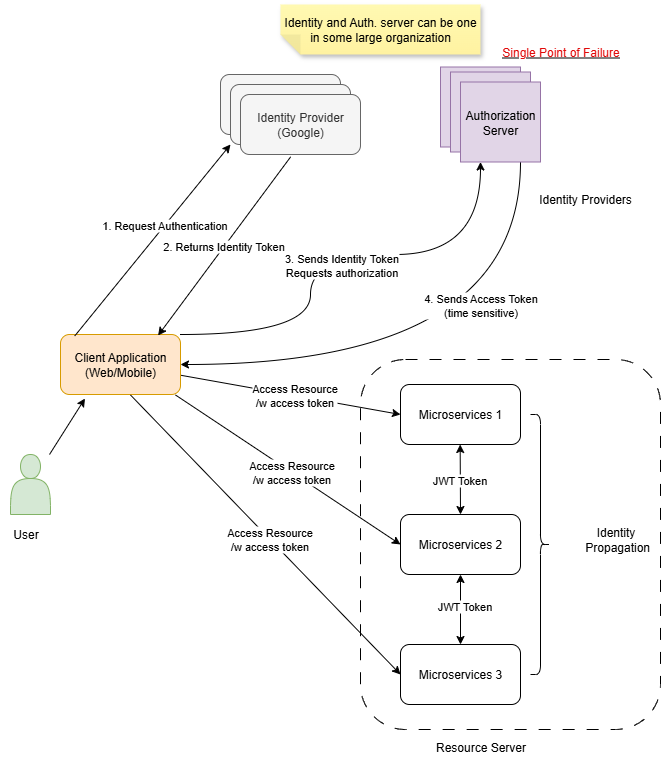
The diagram above illustrates the flow of authentication and authorization using an Identity Provider (like Google), an Authorization Server, and a set of microservices that serve as the resource servers.
1. Key Components
User
The end user who interacts with the application through a web or mobile interface.
Client Application (Web/Mobile)
The application that the user interacts with. This client does not store credentials directly but relies on tokens for authentication and authorization.
Identity Provider (Google)
Responsible for verifying the user’s identity. It issues an Identity Token after successful authentication.
Authorization Server
Grants permission to access resources. It issues Access Tokens that are time-sensitive and scope-limited.
Note: In some organizations, the Identity Provider and Authorization Server are the same system, which can become a single point of failure.
Resource Server (Microservices)
Hosts protected resources and validates incoming requests using access tokens. In this design, multiple microservices communicate with each other by propagating identity through JWT tokens.
2. The OAuth 2.0 Flow
- Request Authentication
The user initiates login via the client application, which sends an authentication request to the Identity Provider. - Identity Token Issuance
The Identity Provider verifies credentials and returns an Identity Token to the client application. - Authorization Request
The client sends the Identity Token to the Authorization Server to request access authorization. - Access Token Issuance
The Authorization Server validates the Identity Token and issues a time-sensitive Access Token to the client application. - Accessing Resources
The client uses the Access Token to call protected APIs on Microservices 1, 2, and 3.- Each microservice validates the Access Token or JWT before fulfilling the request.
- JWT tokens enable identity propagation between microservices, ensuring secure communication in distributed systems.
3. Identity Propagation in Microservices
When microservices need to call each other, they pass along the JWT token issued during the initial request. This ensures that:
- Authorization checks remain consistent across services.
- User identity is preserved without requiring repeated authentication.
- Security is maintained without directly sharing credentials.
4. Potential Risks
- Single Point of Failure
If the Identity and Authorization Server are the same and experience downtime, the entire authentication and authorization process fails. - Token Misuse
Stolen or leaked tokens can be used to impersonate users until they expire.
5. Best Practices
- Separate the Identity Provider and Authorization Server for resilience.
- Use short-lived Access Tokens and refresh tokens for improved security.
- Validate tokens in every microservice.
- Implement proper logging and monitoring to detect suspicious activity.
OAuth 2.0, combined with identity propagation, enables secure, scalable, and user-friendly authentication in distributed systems. By understanding this flow and applying best practices, developers can design systems that are both secure and resilient.
Leave a Reply